Don't give attackers a chance
Data theft, sabotage and cyber extortion are now a tangible threat to everyday business, even for SMBs.
Threats are emerging even in well-protected IT environments. The cybercriminals who are able to overcome effective security protection like yours are also likely to cause the most damage once they are inside.
Also, in many cases, attacks are only discovered after the damage has already been done. Then it's too late!
Information security at all levels ensures that your organisation and your team are well prepared for attacks.
Therefore, make sure that the following areas in your organisation are adequately protected:
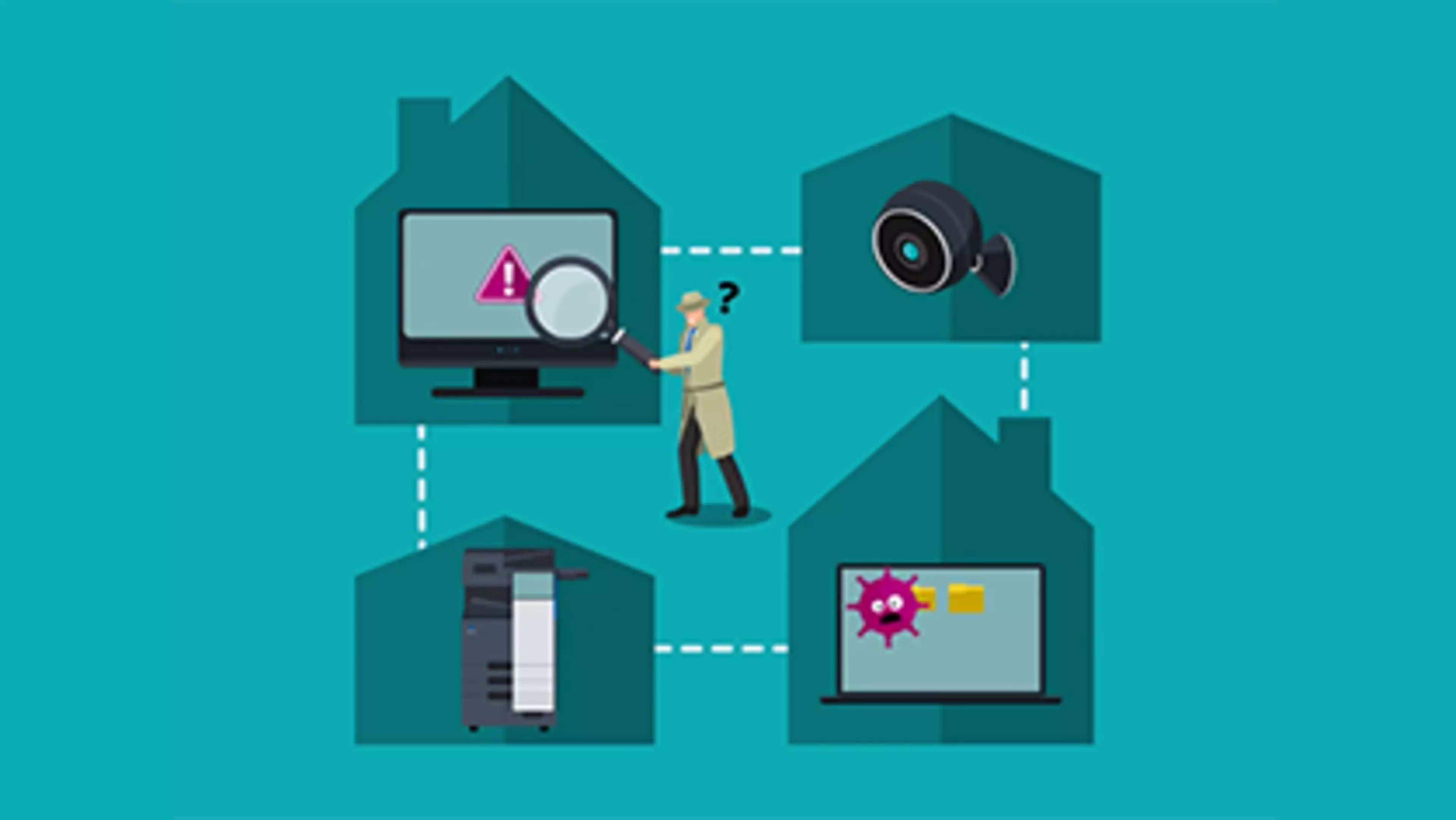
Protect your MFPs from cyber attacks
- MFPs are increasingly becoming the focus of hacker attacks
- Don't make the mistake of neglecting security issues associated with multifunction devices
- Therefore, the areas of access control/access security, hard disc data security and network security should be regulated
- Viruses and malware must be prevented from entering the company network via the MFP
Protect your IT devices from cyber attacks
- Once an attacker has infiltrated your network via a vulnerable endpoint, it can be difficult to identify and stop them
- Protect your IT endpoints such as PCs/laptops, tablets and mobile phones as well as servers, regardless of where your employees work and even when they are not connected to a network
- Detect and neutralise stealthy attacks that have managed to bypass other protective security measures such as passwords and traditional antivirus tools
Protect your identities and data from theft
Ensuring your business continuity
- If you fall victim to a ransomware attack, for example, and the blackmailers hold your data for a ransom, you will not be able to continue your business
- Alternatively, the data is completely lost, in which case restoring the data can be incredibly expensive
- Therefore, the data should be backed up automatically on a daily basis so that the data can be restored quickly in the event of an attack
- This prevents data loss and costly business interruptions
Protection against high fines and loss of reputation
- Your customers' trust is your most valuable asset, and you must not jeopardise it
- Therefore, make sure you have the most effective cybersecurity strategy
- If you do fall victim to an attack and personal data is stolen, you must report this to the authorities and your affected customers within 72 hours in accordance with the GDPR law
- Our solutions help you to comply more easily with the deadlines and requirements for reporting GDPR data breaches
Protection of your physical assets
- Information in a company cannot always only be stolen digitally
- The "classic" way of breaking and entering is also still very common
- Intelligent video surveillance can secure infrastructure, properties or buildings to prevent unauthorised persons from gaining unauthorised access
- They take over the task of constant human monitoring, ensure greater consistency and only involve people (through alerts) when they recognise anomalies, defects, risks or dangers
Your guide to tackling security threats
Read this guide to find out how you should set up your company's security strategy to ensure holistic protection of your information, data and physical assets. It is important for you to know that you are not alone to do that! With Konica Minolta, you have a partner at your side who specialises in small and medium-sized companies and has over 20 years of expertise in the field of security. Our expertise in the area of printer security serves as a basis for us to look at other areas of the company so that you receive 360° protection – all from a single source, so that you are not dependent on several providers. You no longer have to worry about anything, and can instead focus on your core business and plan successfully for the future without disrupting your business.

Further reading

Your guide to NIS2 and what it means for your organisation’s cybersecurity

Why SMBs are most vulnerable to cyber attacks and how you can be better prepared