Ensuring comprehensive security in digital processes is arguably the greatest challenge faced by small and medium-sized companies on a day-to-day basis. Within most organisations, it is hard enough to ensure your own networks, communication systems and storage systems are not compromised, but having to deal with information and data that is out of your control and about which you know little or nothing makes it even more difficult.
However, that is exactly what you have to do to prevent the possible spreading of shadow IT in your company.
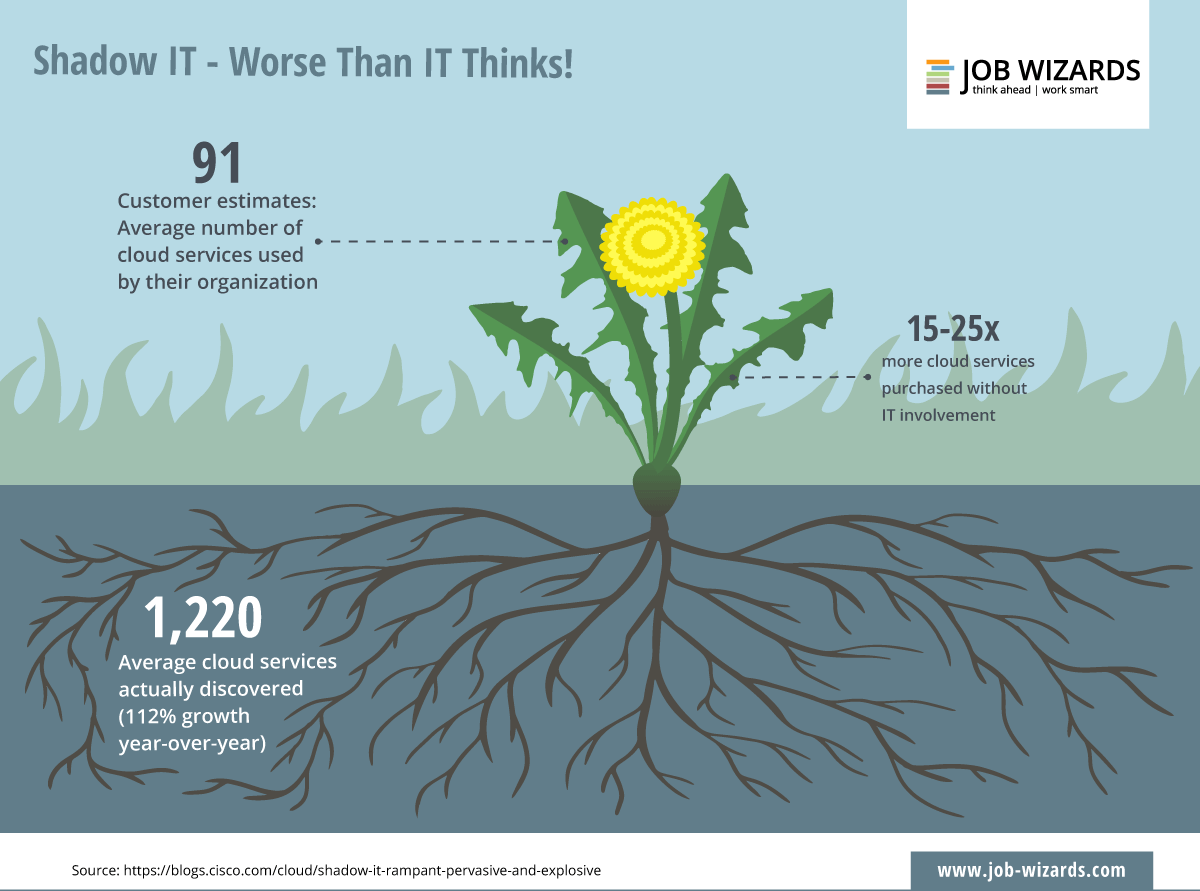
Shadow IT: employees are the greatest source of danger #jobwizards https://km.social/2TDtOoy
If your employees use private software and hardware within the company, they are usually not doing so with evil intentions. ‘Employees simply often look for the most convenient path. This includes using apps, software, and indeed hardware that they are familiar with from their private life. In most cases, they have no sense of wrongdoing,’ says Daniel Schellhase, Senior Product Manager Platform & Technologies at Konica Minolta in Hanover.
An example: someone who wants to send data electronically from their workplace, but then realises that the company IT limits the size of file that can be sent, will reach for the solution that they also use among family or friends, to send photos, for example. In many cases, that is Dropbox or WeTransfer. The problem: the files are not stored on the company servers and could fall into the wrong hands.
Paths out of the shadows
However, it is not only software use that presents a shadow IT risk. When employees – often with the encouragement of their employer – use their own smartphones, tablets or laptops, the company loses control. ‘BYOD’ (Bring Your Own Device) allows employees to follow the most convenient path, but takes security guidelines into a cul-de-sac, because if the employee ever leaves the company, the data will be irretrievably lost.
Companies need to look for new solutions to prevent employees making use of their own. But what is the right approach? ‘The company has to offer things that eliminate the employees’ desire to make use of shadow IT,’ explains Daniel Schellhase. ‘But before that, companies must ask themselves five questions.’
Are we agile enough?
- An example: if employees can work better on tablets, can the company make them available quickly and easily?
Are we adaptable enough?
- An example: is the company in a position to be able to change to faster and better systems if the current ones do not meet the requirements?
Do we have the necessary budget?
- An example: how much is the security of our structures and systems worth and how sustainable is a possible solution?
Do our employees understand the requirements?
- An example: if employees are not aware of the dangers of using shadow IT, targeted clarification is required.
How do we work together with external partners?
- An example: can we find a shared platform for cooperation with each other, as well as with external partners and customers?
‘The last point in particular is indispensable for sales organisations or companies with field sales representatives. They need a tool to keep them in constant contact with their headquarters and all relevant departments. This allows them to access information directly when talking to a customer, for example,’ says Daniel Schellhase.
dokoni SYNC & SHARE from Konica Minolta makes it possible to read, write, edit, send, share and archive documents from anywhere, at any time and on any device.
Thus, there are solutions to the problems and challenges that accompany shadow IT, allowing companies to fulfil their own security requirements – without diverting employees from their preferred (convenient) path.